Vulnerability Analysis
Detect and Mitigate Application Vulnerabilities Quickly

Vulnerability Detection & Mitigation Challenges
As developers increasingly rely on third-party APIs, SDKs, and open-source code, they inadvertently expose their applications to known or zero-day vulnerabilities, which are difficult to track and resolve
-
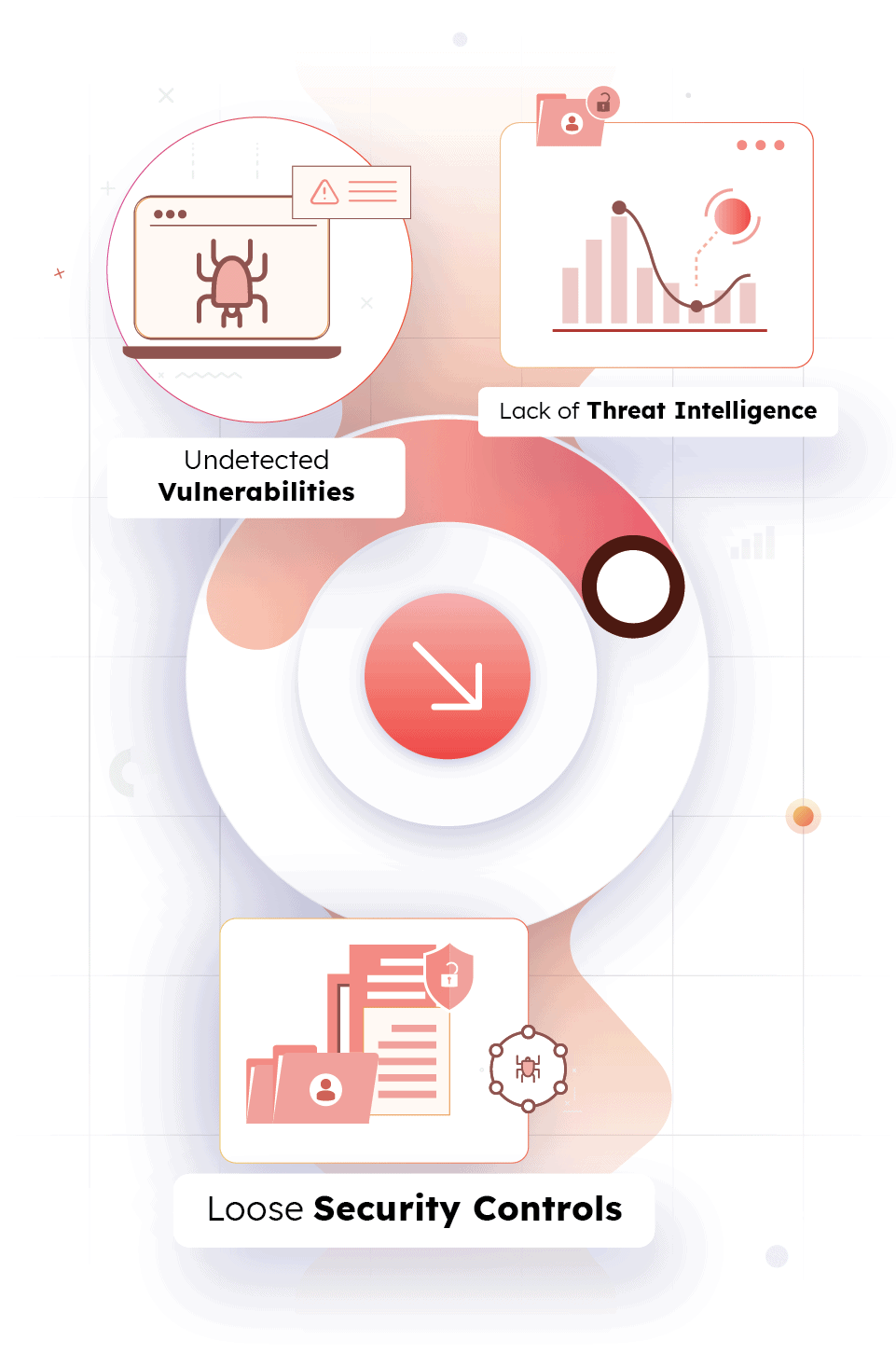
Undetected Vulnerabilities
Known vulnerabilities in third-party code often remain undetected as they aren’t scanned or updated/patched in a timely manner.
-
Lack of Threat Intelligence
Organizations fail to quickly integrate threat intelligence from different sources, which makes signature-based threat detection ineffective.
-
Loose Security Controls
The inability to enforce encryption, code obfuscation, AAA policies, and other security best practices and lack of traceability and anomaly detection capabilities make mitigation of vulnerabilities challenging.
Automate Vulnerability Scanning
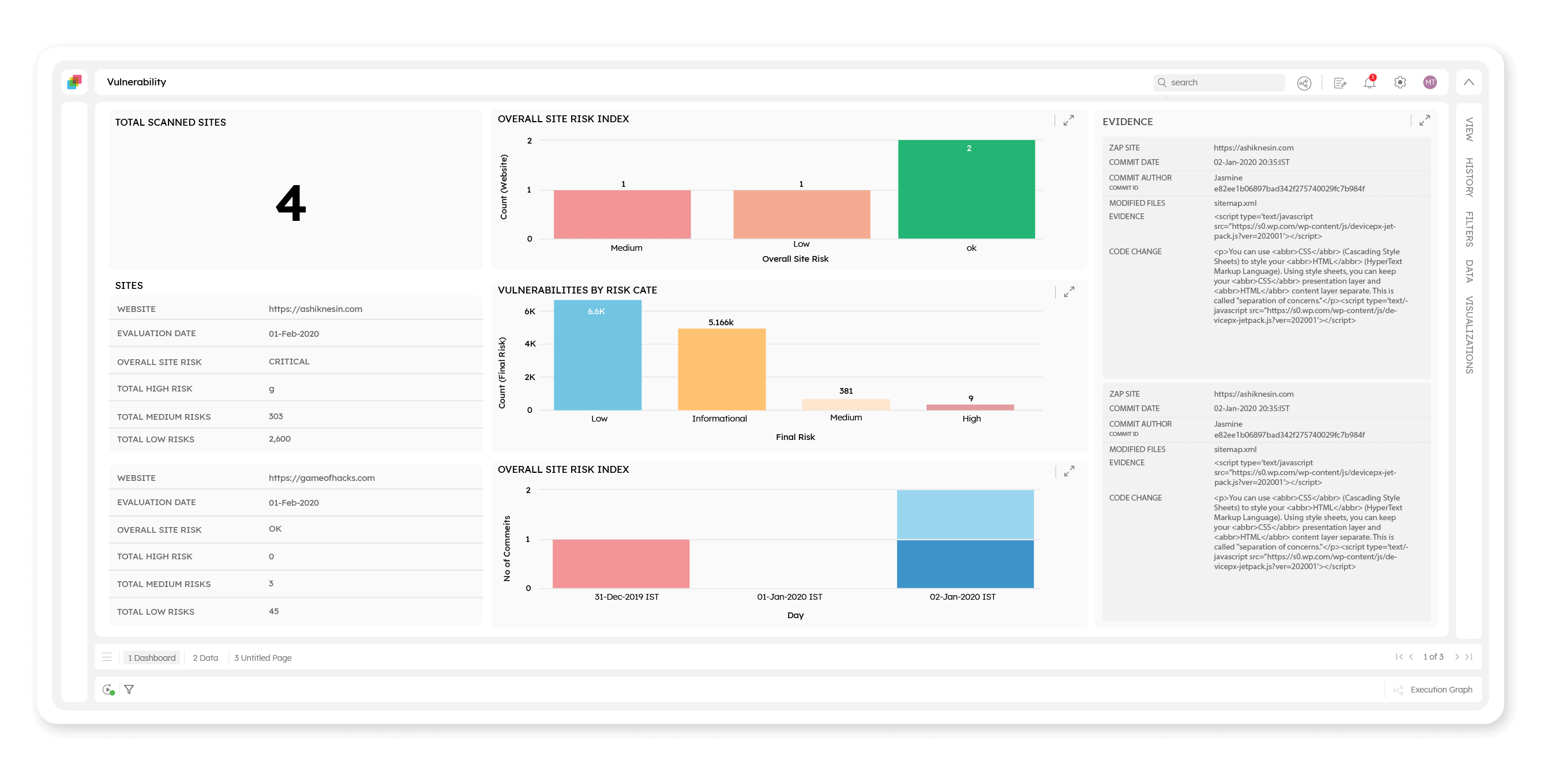
Track, diagnose, and resolve application vulnerabilities with automated vulnerability scanning, reducing your exposure to threats across third-party or open-source components, widgets, and libraries.
-
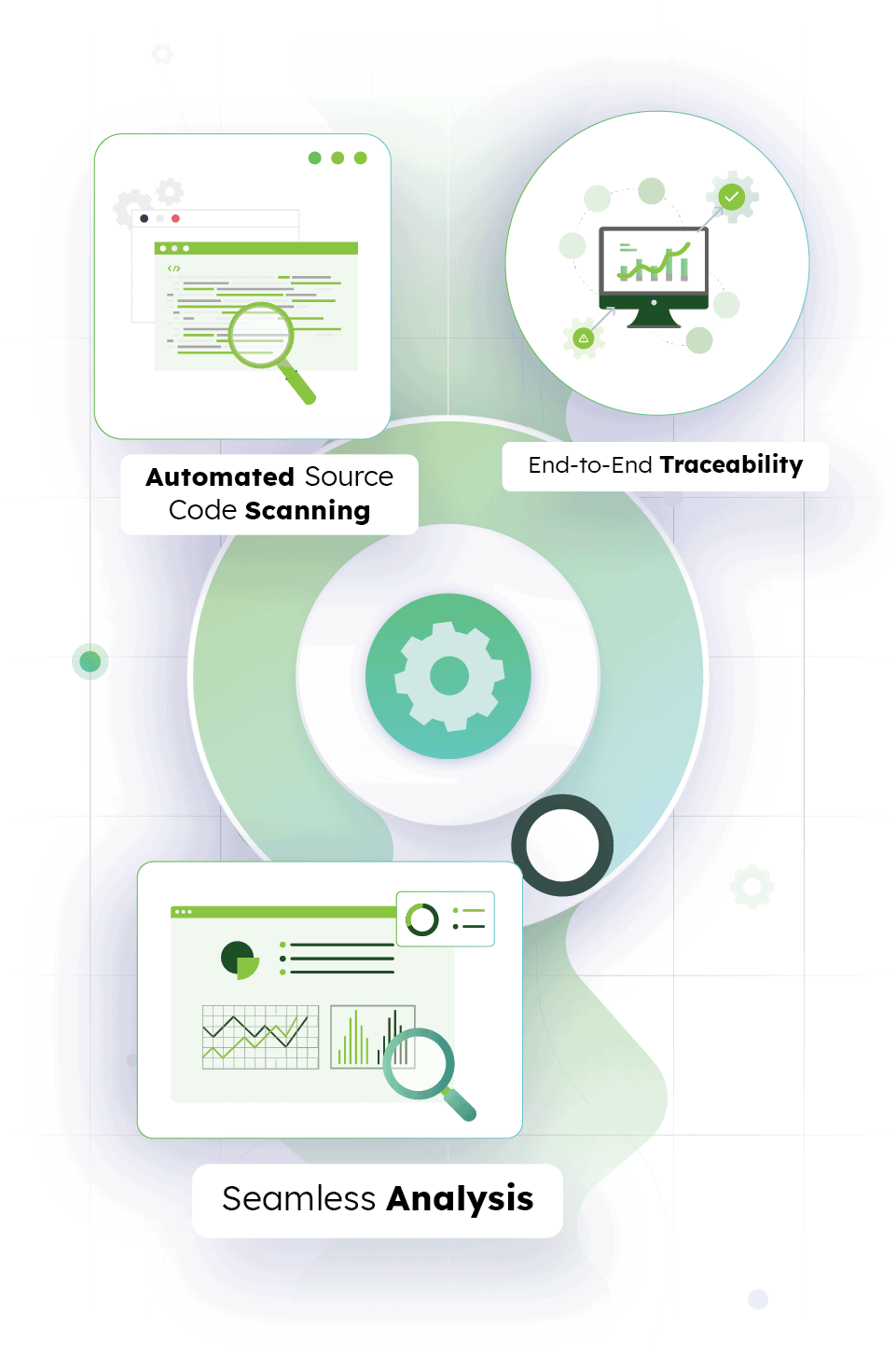
Automated Source Code Scanning
Scan applications as per predefined schedule with OWASP ZAP to detect vulnerabilities.
-
End-to-End Traceability
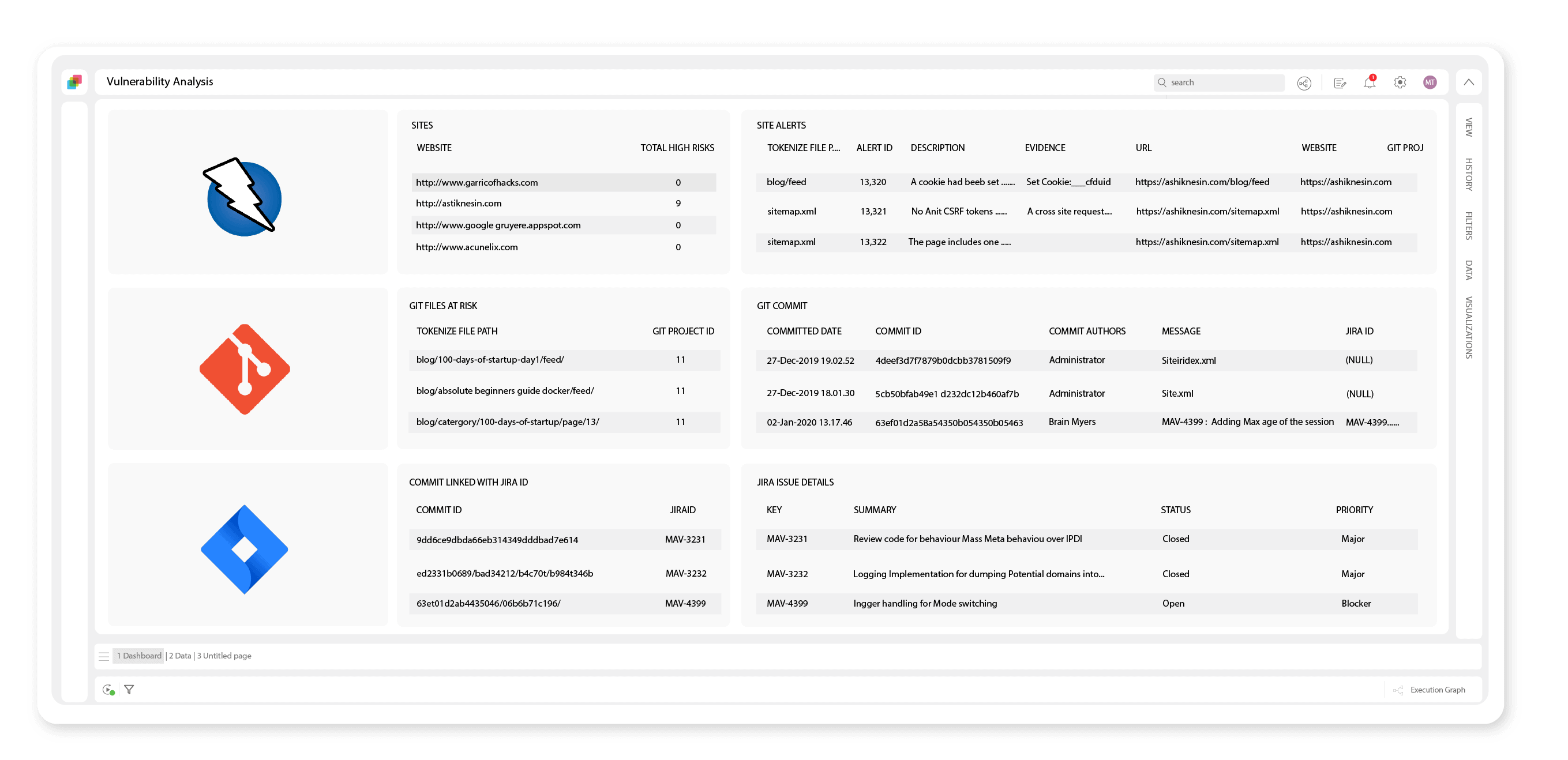
Trace the vulnerabilities to their corresponding lines of code in the source code repository for a quick resolution.
-
Seamless Analysis
Drill down to associated issues in Jira to find out who’s responsible or who can resolve the issue. Identify all associated and potentially impacted features and components.
Unify Security Monitoring
Gathr’s out-of-the-box app for vulnerability analysis improves your application security by integrating various tools across CI/CD and Cloud tech stack and improving security observability and controls:
-
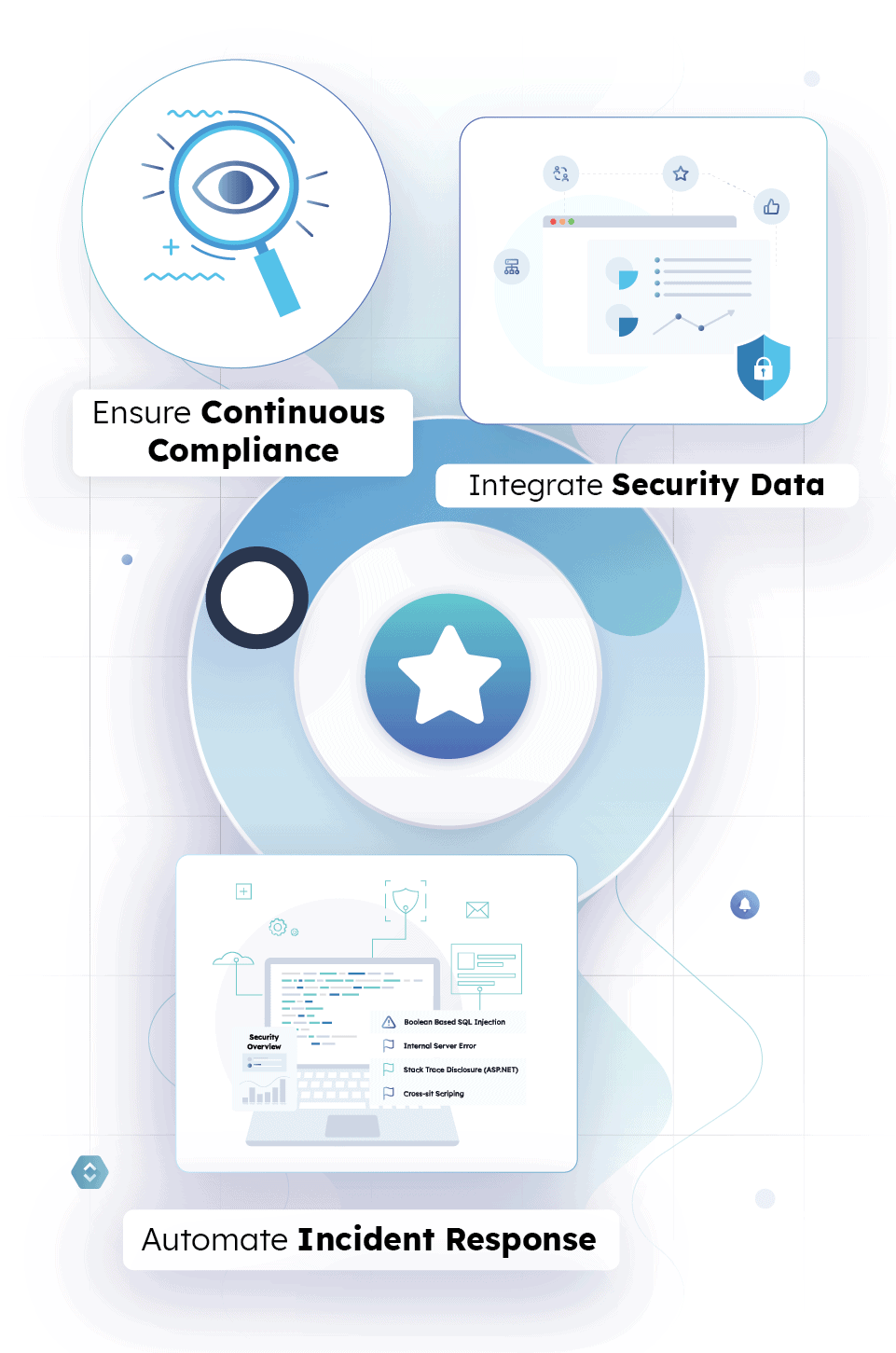
Ensure Continuous Compliance
Visually track the percentage of changes following the pipeline tools, PR approvals, and peer reviews; learn more.
-
Integrate Security Data
Collect and analyze data from threat intelligence feeds, application logs, Security, Information, and Event Management Tools (SIEM) tools, and more.
-
Automate Incident Response
You can automate incident response playbooks with advanced alerts, workflows, and ticket generation to ensure a quick, coordinated response.
Solution Highlights
-
Ready-to-use solution requiring minimal configuration
-
Out-of-the-box connectors to gather and analyze data from multiple tools
-
Ready dashboards and templates to visualize data
-
Python and Machine Learning support for predictive analysis
-
Highly flexible; change formulas and add new tools without coding
Solution Benefits
Release Go/No-Go solution helps teams expedite their release lifecycle with dashboards providing actionable insights suited for different stakeholders as per their context.
Engineering Services
Explore Other Solutions
Gathr offers a host of ready-to-use apps and solutions to address your workflow, process automation, and analytics needs.
Get a Holistic View of DevOps Unifying Both Application & Infrastructure Data
View DetailsTrack the Effectiveness of your Development and Delivery Processes Across DORA Metrics
View DetailsTroubleshoot Defects and Vulnerabilities Faster with End-to-End Traceability
View Details