Code Leak Analysis
Detect Code Leaks Across Public Repositories

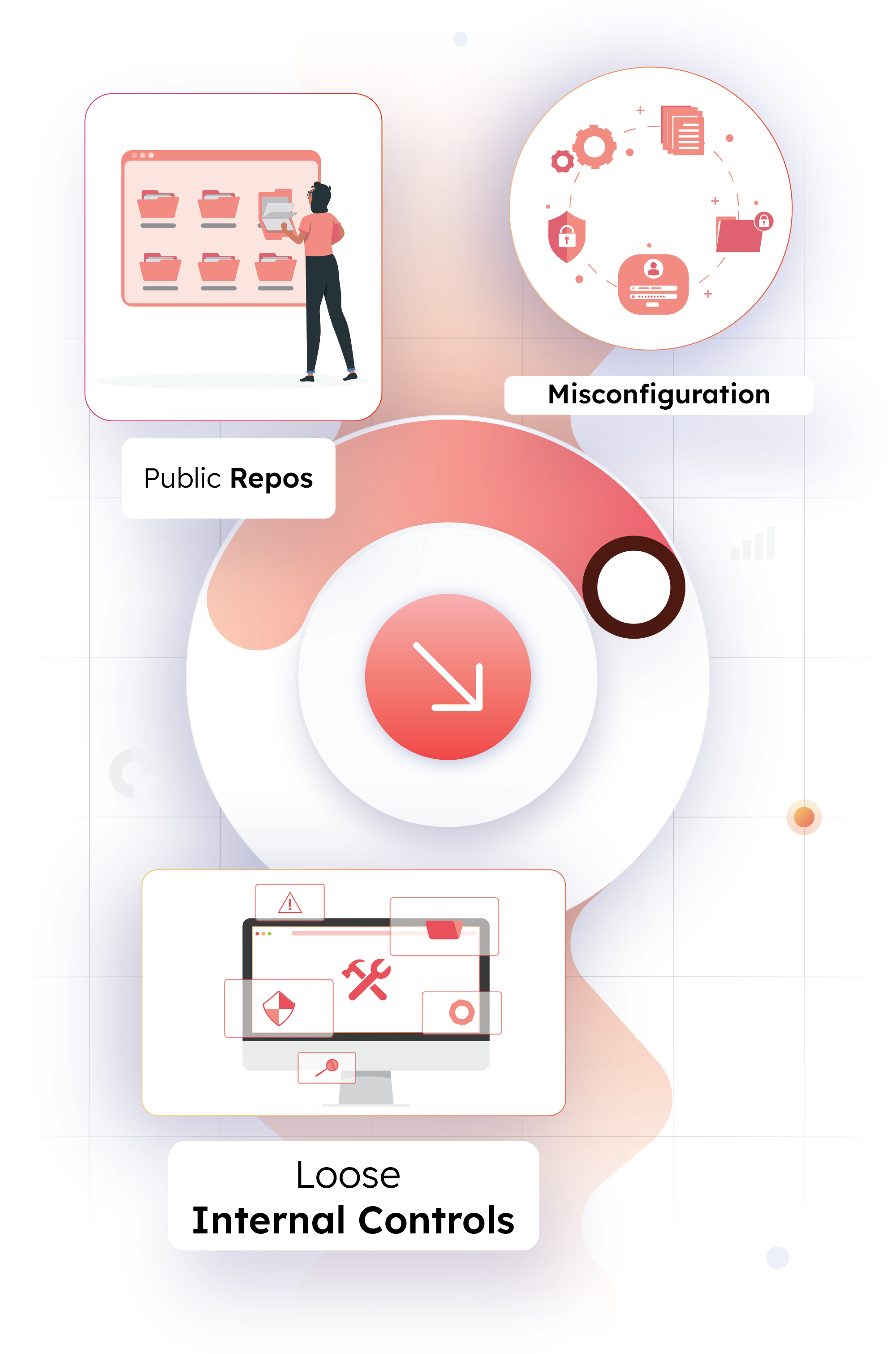
Source Code Leak Challenges
With multiple ongoing projects, enterprises often struggle to enforce and monitor development best practices, security policies, peer reviews, and other measures to maintain source code security and integrity, which proves to be costly:
-
Public Repos
As developers frequently rely on public code repositories and share code snippets with each other, they inadvertently expose secrets or inherit vulnerable pieces of code.
-
Misconfiguration
Many times, misconfiguration, inadequate access controls, and logic flaws in the source code allow threat actors to get access to critical customer information, passwords, keys, etc.
-
Loose Internal Controls
Organizations fail to implement best practices for secure collaboration, such as encryption, code obfuscation, the principle of least privilege, etc., allowing secrets to fall into the wrong hands.
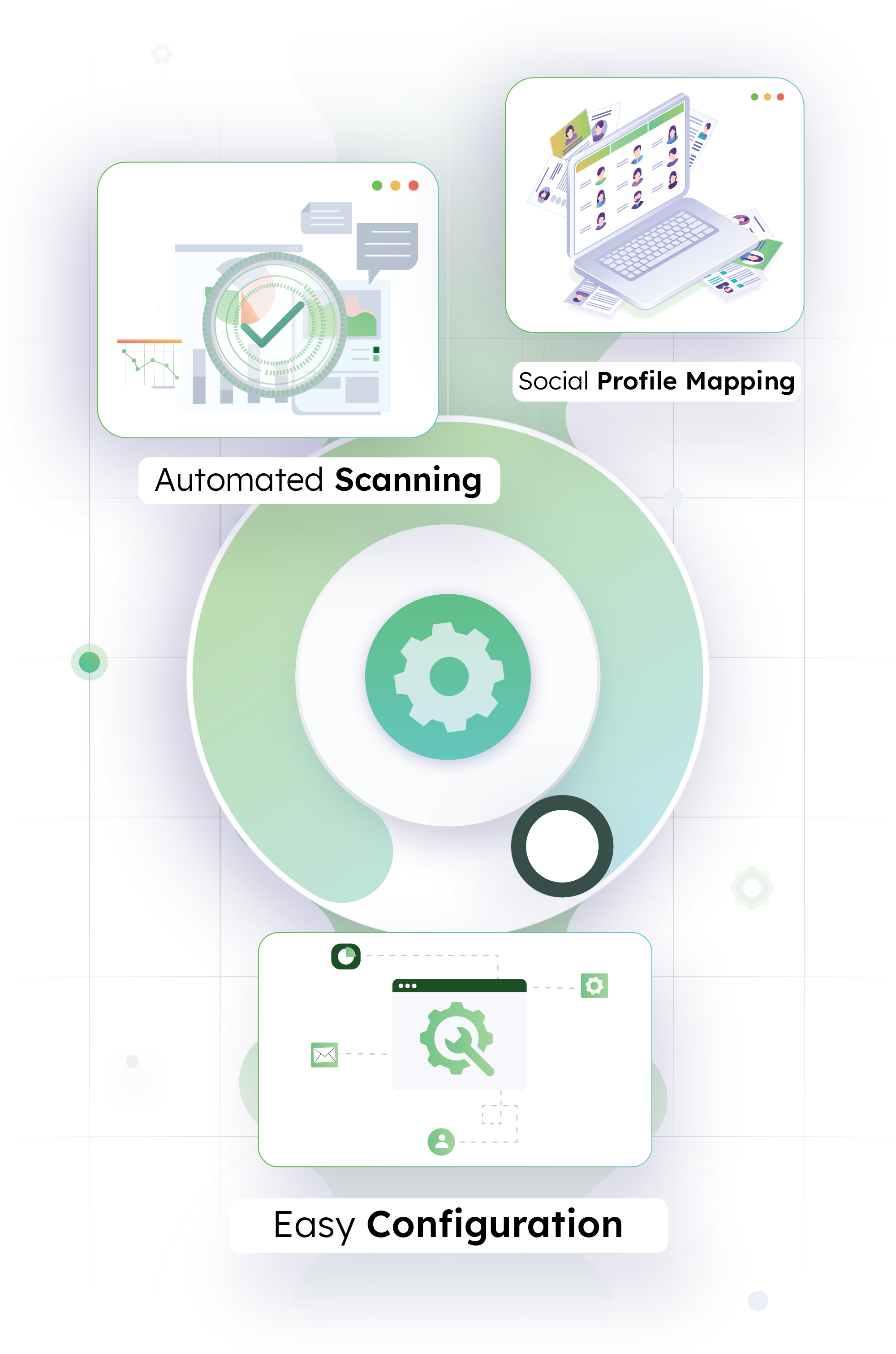
Automate Source Code Leakage Monitoring
Detect source code leaks across open-source, public repositories such as GitHub and prevent your application code and critical data from falling into the wrong hands
-
Automated Scanning
Scan public Git repositories to detect if any of your private code containing critical passwords, API keys, and tokens is exposed.
-
Social Profile Mapping
Identify Git authors and run scans to find their social profiles and map them to your internal employee database.
-
Easy Configuration
Define rules/patterns to run scheduled code scans and get alerts for source code leaks via email, slack, or any other preferred notification service/tool.
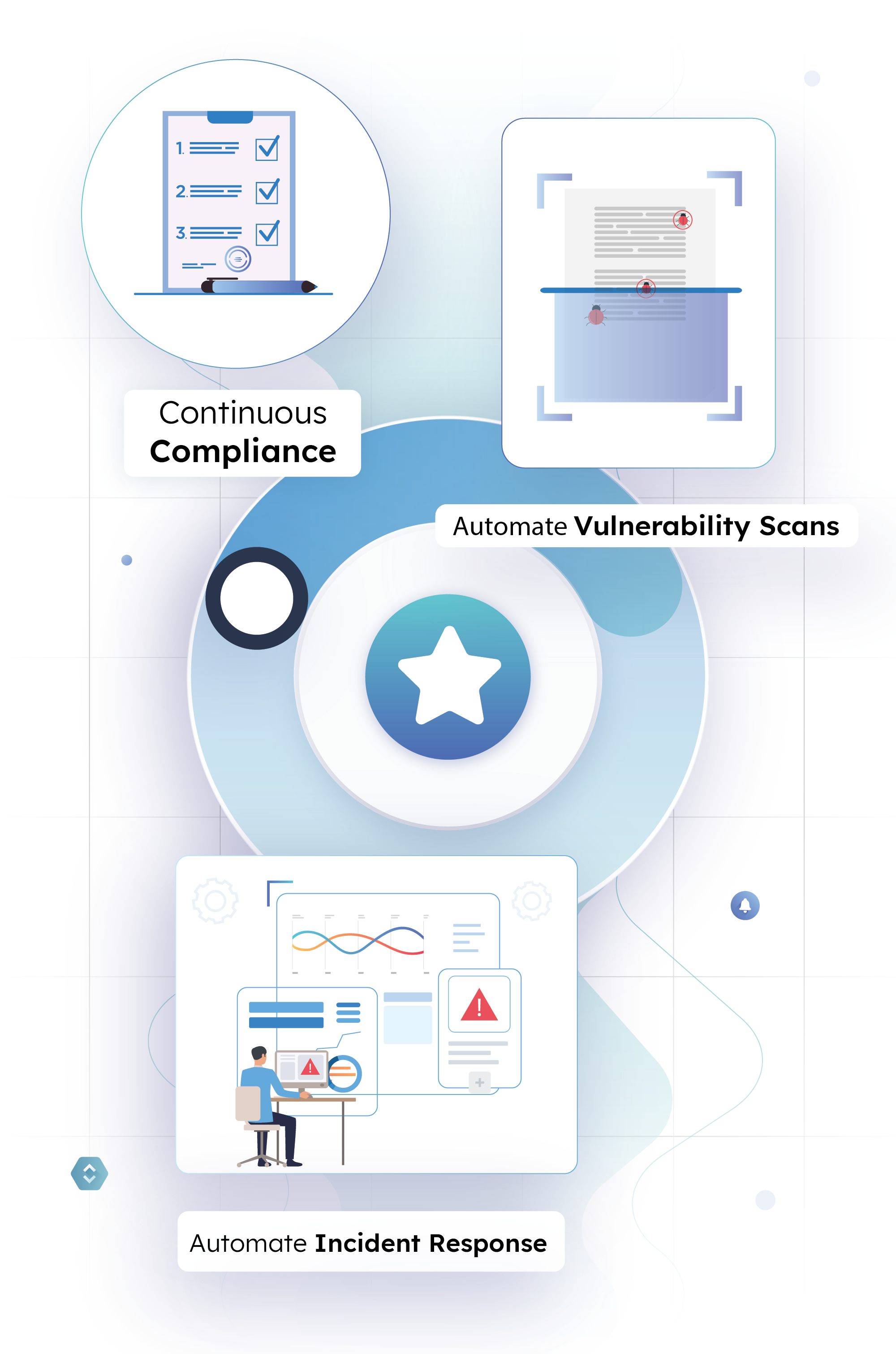
Enhance Application Security
Improve your security posture with proactive centralized monitoring and automated incident response by connecting with various tools in your tech stack
-
Continuous Compliance
Visually track the percentage of changes following the pipeline tools, PR approvals, and peer reviews; learn more.
-
Automate Vulnerability Scans
Scan applications as per predefined schedule with OWASP ZAP to detect vulnerabilities; learn more.
-
Automate Incident Response
You can automate incident response playbooks with advanced alerts, workflows, and ticket generation to ensure a quick, coordinated response.
Solution Benefits
The detection and resolution of source code leaks can prevent your business from severe reputational and financial losses.
Cloud Communication
Explore Other Solutions
Gathr offers a host of ready-to-use apps and solutions to address your workflow, process automation, and analytics needs.
Track the Effectiveness of your Development and Delivery Processes Across DORA Metrics
View DetailsTroubleshoot Defects and Vulnerabilities Faster with End-to-End Traceability
View Details